On May 12, 2017 a new strain of the Ransom.CryptXXX (WannaCry) strain of ransomware began spreading widely impacting a large number of organizations, particularly in Europe.
Hours after the malware that affected the National Health Service (NHS) England spread to as many as 74 countries, the United States Department of Homeland Security (DHS) released a statement saying it was “aware of reports of ransomware known as WannaCry affecting multiple global entities.”
The DHS noted that Microsoft released a patch in March that addresses this vulnerability, adding, “individual users are often the first line of defence against this and other threats, and we encourage all Americans to update your operating systems and implement vigorous cybersecurity practices at home, work, and school,” The Guardian reports.
The DHS said it was also “actively sharing information related to this event and stand ready to lend technical support and assistance as needed to our partners, both in the United States and internationally.”
The agency further said it was working with chief information officers in other U.S. federal departments to ensure “our own networks are protected against the threat.”
Earlier, a security expert at Surrey university claimed that the malware resembled an exploit of ‘EternalBlue’.
‘EternalBlue’ is the name given to a weakness in Microsoft’s security that is thought to have been identified secretly by the United States National Security Agency (NSA).
“From the analysis that has been done, it looks like it is the ‘EternalBlue’ weakness that has been exploited because it is using the same ports and protocols. We don’t know publicly if it is the NSA (that found the vulnerability) but it is widely assumed it is and that is what Shadow Brokers said,” The Guardian quoted Prof. Alan Woodward, as saying.
This particular vulnerability was publically disclosed by a group calling itself Shadow Brokers, which claimed to have stolen it from the NSA, among a cache of files it took.
Meanwhile, Kaspersky Lab, a cybersecurity company based in Moscow, published a blog post in which it estimates that 45,000 attacks have been carried out in 74 countries, mostly in Russia.
It added that the totals could be “much, much higher.”
Earlier, a number of hospitals across England were forced to divert emergency patients after being hit by a suspected cyber attack.
Attacks then began being reported across many other countries, including Turkey, Vietnam, the Philippines, Japan, the U.S., China, Spain, Italy and Taiwan with the majority of affected computers in Russia.
The computers all appeared to be hit with the same ransomware, and similar ransom messages demanding about $300 to unlock their data, The New York Times reported.
Source : (ANI)
What does ransomware do
Crypto-ransomware encrypts the files on a computer, essentially scrambling the contents of the file so that you can’t access it without a decryption key that can correctly unscramble it. A ransom is demanded in exchange for the decryption key. Once the malware has infected one computer, it can spread to others in the network, making it impossible to carry out normal operations. The ransom fee is usually around USD 300 to USD 500 for a computer, and payment is often demanded in Bitcoins, a virtual currency that is difficult to trace.
How can ransomware infect your computer
You may encounter ransomware in a number of ways: as email attachments, malicious links, or via exploit kits. You can be exposed to exploit kits when you visit a compromised website, click a compromised ad on an otherwise good website or you are redirected onto a malicious site. The exploit kit tests your computer for any exploitable flaws or vulnerabilities, which are common in outdated software. If it finds an opening, the exploit kit downloads and installs the ransomware onto your machine. This can happen completely without your knowledge.
What is the WannaCry ransomware?
WannaCry encrypts data files and ask users to pay a US$300 ransom in bitcoins. The ransom note indicates that the payment amount will be doubled after three days. If payment is not made after seven days, the encrypted files will be deleted.

It also drops a file named !Please Read Me!.txt which contains the text explaining what has happened and how to pay the ransom.
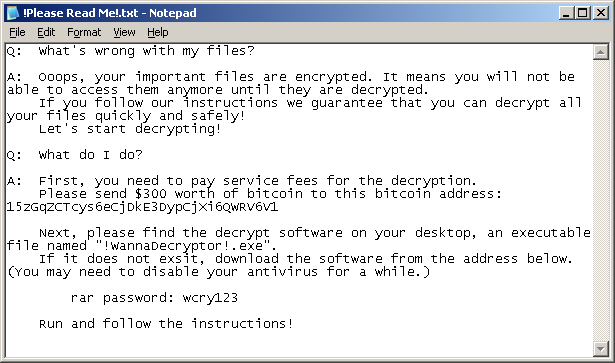
WannaCry encrypts files with the following extensions, appending .WCRY to the end of the file name:
- .lay6
- .sqlite3
- .sqlitedb
- .accdb
- .java
- .class
- .mpeg
- .djvu
- .tiff
- .backup
- .vmdk
- .sldm
- .sldx
- .potm
- .potx
- .ppam
- .ppsx
- .ppsm
- .pptm
- .xltm
- .xltx
- .xlsb
- .xlsm
- .dotx
- .dotm
- .docm
- .docb
- .jpeg
- .onetoc2
- .vsdx
- .pptx
- .xlsx
- .docx
It propagates to other computers by exploiting a known SMBv2 remote code execution vulnerability in Microsoft Windows computers: MS17-010
Intrusion Prevention System
- 21179 (OS Attack: Microsoft Windows SMB Remote Code Execution 3)
- 23737 (Attack: Shellcode Download Activity)
- 30018 (OS Attack: MSRPC Remote Management Interface Bind)
- 23624 (OS Attack: Microsoft Windows SMB Remote Code Execution 2)
- 23862 (OS Attack: Microsoft Windows SMB Remote Code Execution)
- 30010 (OS Attack: Microsoft Windows SMB RCE CVE-2017-0144)
- 22534 (System Infected: Malicious Payload Activity 9)
- 23875 (OS Attack: Microsoft SMB MS17-010 Disclosure Attempt)
- 29064 (System Infected: Ransom.Ransom32 Activity)
Organizations should also ensure that they have the latest Windows security updates installed, in particular MS17-010 to prevent spreading.
What are best practices for protecting against ransomware?
- New ransomware variants appear on a regular basis. Always keep your security software up to date to protect yourself against them.
- Keep your operating system and other software updated. Software updates will frequently include patches for newly discovered security vulnerabilities that could be exploited by ransomware attackers.
- Email is one of the main infection methods. Be wary of unexpected emails especially if they contain links and/or attachments.
- Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros and instead immediately delete the email.
- Backing up important data is the single most effective way of combating ransomware infection. Attackers have leverage over their victims by encrypting valuable files and leaving them inaccessible. If the victim has backup copies, they can restore their files once the infection has been cleaned up. However organizations should ensure that back-ups are appropriately protected or stored off-line so that attackers can’t delete them.
- Using cloud services could help mitigate ransomware infection, since many retain previous versions of files, allowing you to “roll back” to the unencrypted form.